Like road traffic, it is essential to identify the cause of the slowdown to act and restore order. In the case of a computer network, the frustrating question that runs: Who is monopolizing my bandwidth?
If you are noticing that your Internet speeds are not what they used to be, the reason could be employees constantly listening to streaming music or watching online movies. Not only does having an entire office streaming media influence your bandwidth, but employees also watching movies or TV can really kill productivity.
The struggle to prevent misuse of the internet in the workplace has been a long challenge to overcome. Recent studies demonstrate that upwards of 25% of Internet bandwidth in an office are consumed by employees misusing the internet. From social media and chatrooms to video games and video streaming, employees face limitless temptations and risks when they log on to their work computer and hop online.
According to an International Data Corporation (IDC) report 30% – 40% of Internet use in the workplace is unrelated to business. When an employee browses across the internet, they can unknowingly visit one of the thousands of malicious websites that are being registered daily. These cybersecurity threats can be just as devastating for a company as any amount of lost productivity.
On top of all the ways of misusing internet at workplace, increasing number of crypto mining activities at workplace not only slowdown the network but also lead to increased electricity costs and damaged hardware.
The Network Traffic Analyzer (NTA) module of the blësk network monitoring tool, captures the continuous flow of network traffic and presents the data in graphs and tables. These can provide valuable information on how your network is being used. It is a simple, portable traffic measurement and monitoring tool, which supports various management activities, including network optimization & planning, and detection of network security violations.
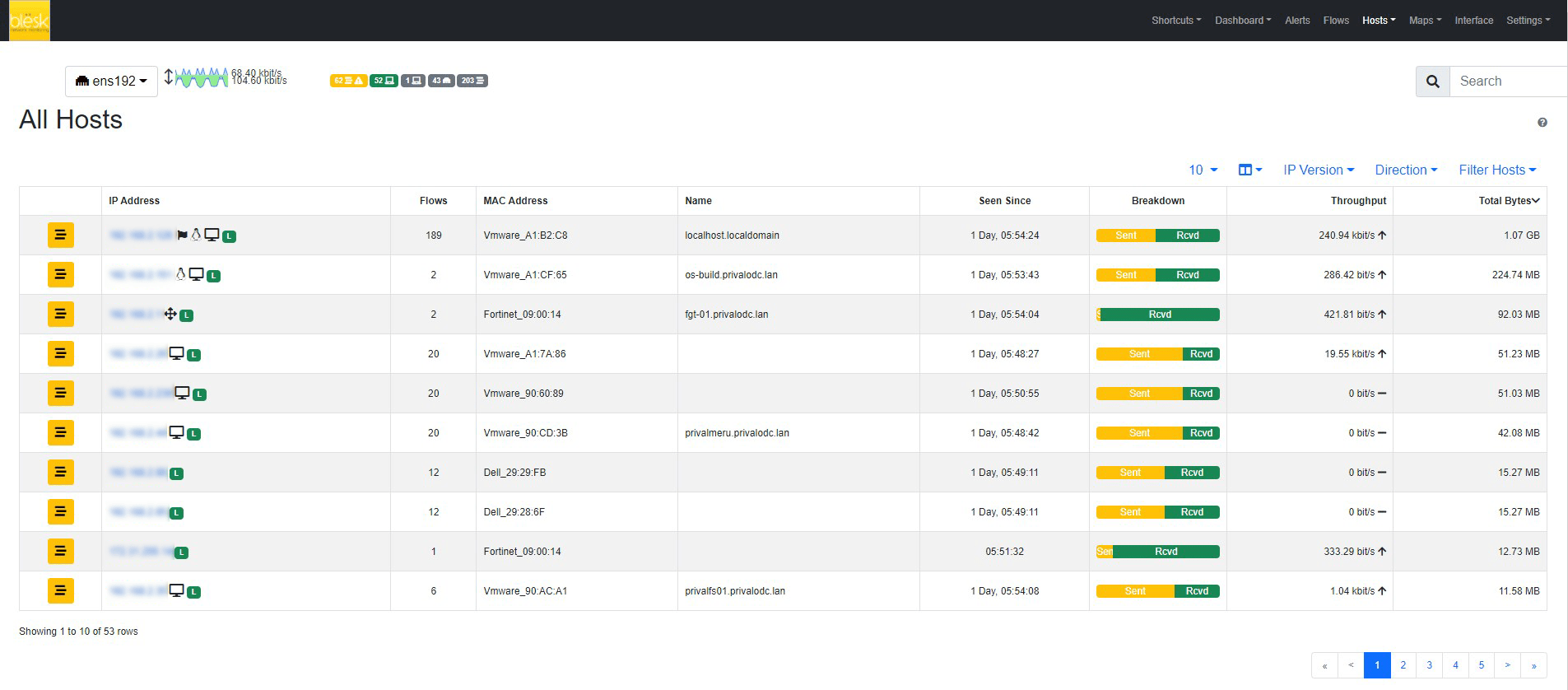
blësk NTA helps the network administrators keep a close eye on network perimeter. Even with strong firewalls in place, mistakes can happen, and unwanted traffic could get through. Users could also leverage methods such as tunneling, external anonymizers, and VPNs to get around firewall rules.
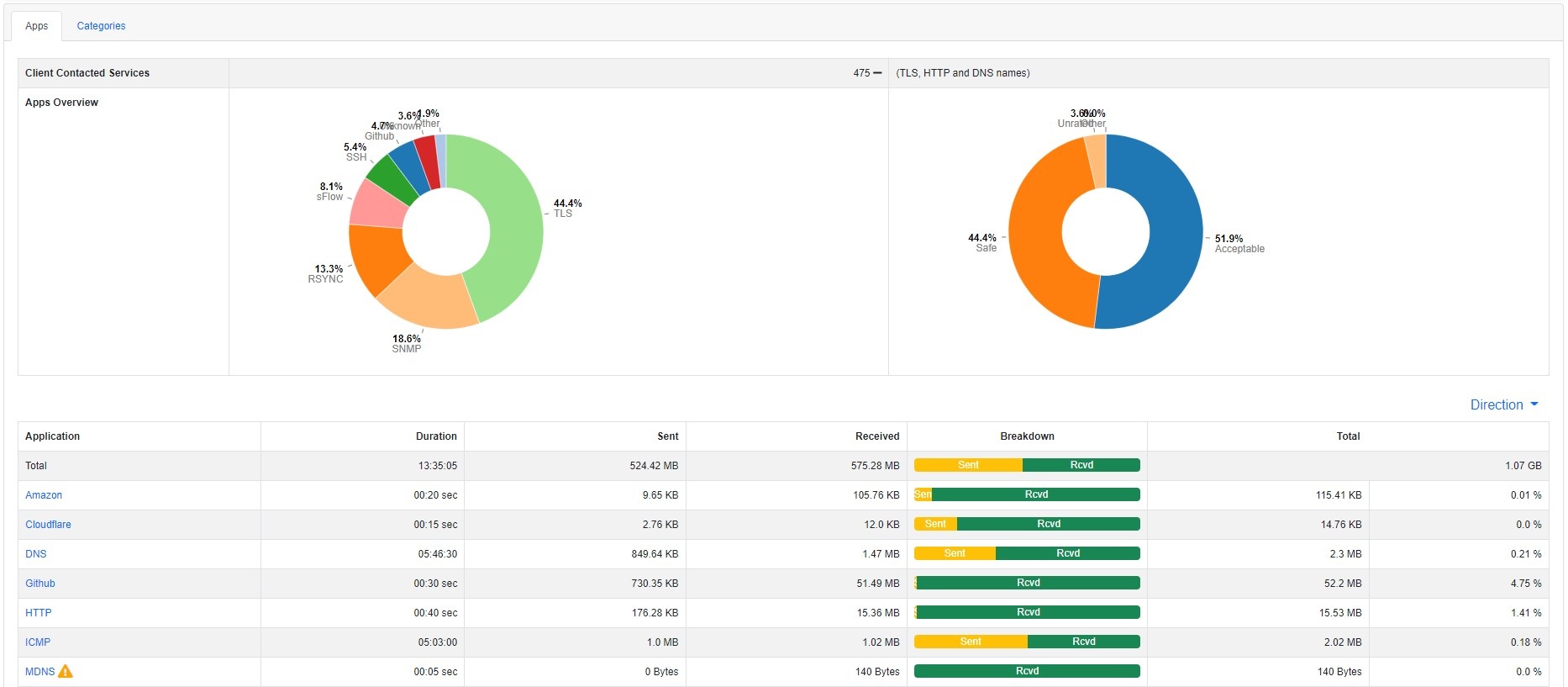
NTA provides the ability to identify those situations where network traffic does not comply with specified policies, or when it exceeds defined thresholds. This will help you in detecting network configuration problems including:
- Misconfiguration of software applications (by analyzing protocol traffic data)
- Identification of hosts that use unnecessary protocols.
- Excessive network bandwidth utilization
blësk NTA discovers the application protocols (Facebook, YouTube, BitTorrent, etc.) using the nDPI approach, a deep packet inspection technology. It characterizes HTTP traffic by relying, among other
things, on the characterization services provided by Google (search engines rather than Google?).
It provides detailed information about network traffic, including traffic volume, key speakers, bandwidth consumption, and high usage times.
blësk NTA is compatible with all data capture approaches necessary for the functionality of this type of software. It can use flow data statistics generated by routers, switches, specialized standalone hardware probes, or mirror port configuration on switches.
Briefly blësk NTA is an essential way to monitor network availability and activity to identify anomalies, maximize performance, and keep an eye out for attacks.
We understand that some organizations may not have inhouse capacity to facilitate many essential tasks; therefore, blësk offers managed services for the low resourced companies to monitor their network services.
Download a free trial of blësk or contact us for more information.