Software vulnerabilities have been widespread since the beginning of the Internet. Despite the evolution of IT security platforms, software and systems can never be claimed as completely secured. A software vulnerability is an existing glitch or flaw that is present in software including operating systems like Android, Windows, Linux or Mac.
With the succession of technologies related to IT security, hackers are also getting smarter and they can discover these loopholes.
A 2021 report shows that the year 2021 had the highest average cost in 17 years due to data breaches worldwide caused by security vulnerabilities. For the healthcare sector in 2021 the average cost was $9.23 million.
Precautionary security measures can help businesses prevent the intrusion of hackers into their system that can leverage the existing security flaws of the applications.
Some of these measures include:
- Assess existing and emerging vulnerabilities
- Run routing software vulnerability tests
- Implementation of a well configured firewall
- Establish a well functioning security monitoring system
- Monitor the performance of the network
- Closely analyze network traffic on the real time
There are many applications in the market one can use to improve the security posture and prevent vulnerabilities in a network. However, the security monitoring process is cost and resource intensive and often unaffordable.
blësk is a cost-effective and complete all in one network monitoring package that will help your organization monitor and prevent software vulnerabilities, which in turn help will help you prevent unauthorized intrusion to your network.
blësk’s Network Security Monitor (NSM) provides a way to continually identify potential vulnerabilities on systems and produces a detailed plan on how to remediate and remove those vulnerabilities from your critical business systems.
The NSM function, allows to automatically scan a subnet of a network based on a custom schedule and it automatically reports the results to the administrator by email in different formats. The NSM module allows to define targets for vulnerability scans, which may be a single IP or range of IP addresses to execute NVT script towards targeted system(s) to test for vulnerabilities and it allows to schedule the frequency of running the test.
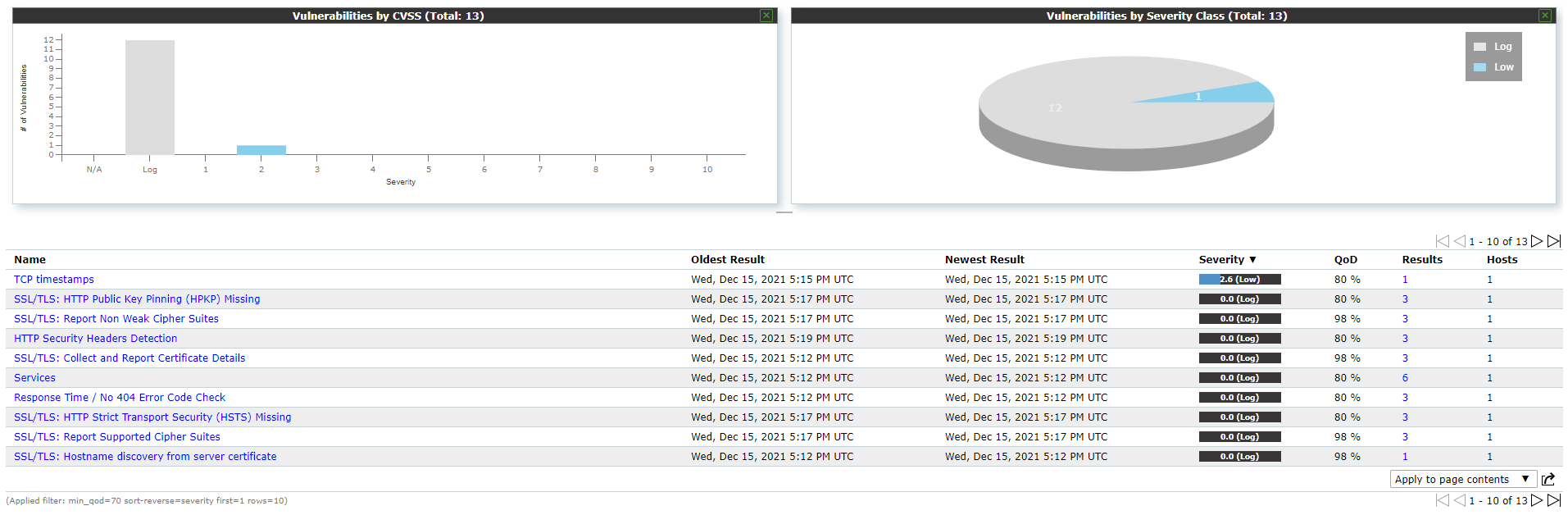
The Network Security Monitor allows to create infinite custom dashboards for groups of devices for the ease of monitoring devices by device type.
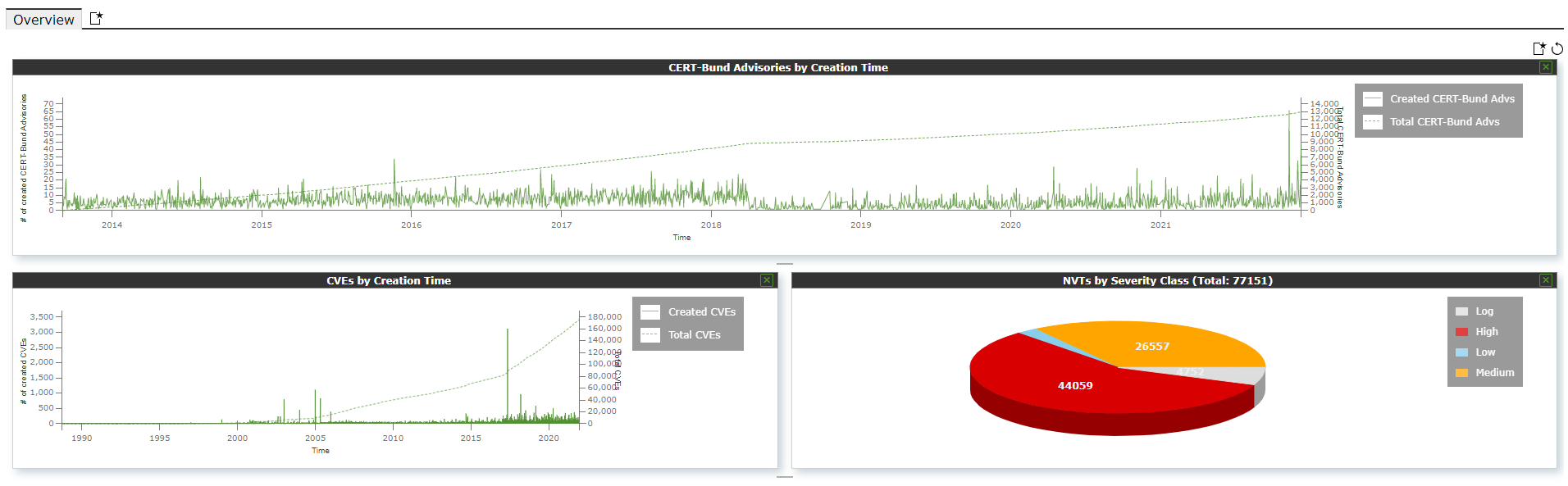
Network Security Monitor (NSM) runs vulnerability tests using the updated vulnerabilities found in the Common Vulnerabilities and Exposures (CVE) reference database as well as CPEs, OVAL, and CERT.
blësk also offers managed services to companies that do not have enough resources to monitor their network.
Download a free trial of blësk or contact us for more information.